Now a lot of people are using Cloudflare because of their Web application firewall. But I saw a Big problem in the Integration which most people has.
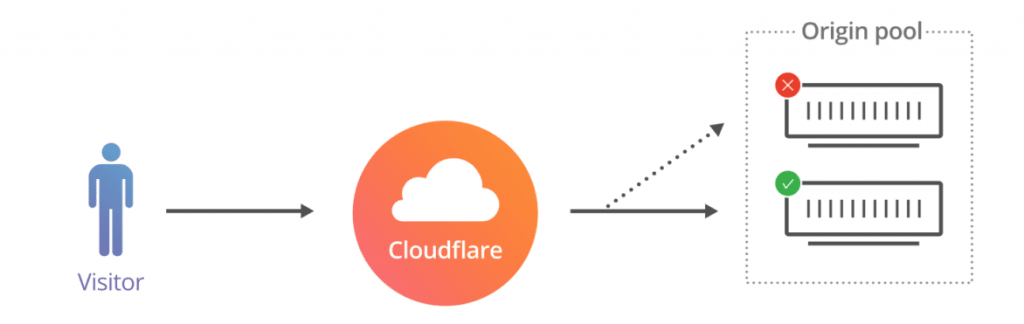
If you want to use Cloudflare services, as per their policy you must point your name servers to Cloudflare. So the Protection Of Cloudflare is Deployed in the DNS level.
When you are making a connection to a website which the DNS is hosted in Cloudflare, you will be connected to Cloudflare network and then it will connect you to the Origin web server.
The Traffic flow is Visitor => Cloudflare network => Origin server. All the traffic(web) should be routed through the Cloudflare network. So Cloudflare will act as a tunnel between your Visitor and server.
When you use the Cloudflare proxy (see the screenshot below) in your DNS, 2 Cloudflare proxy IPs are published to DNS Instead of your Origin server’s IP. So you can keep your Origin servers IP as private.
Why should keep Your origin server IP secret ? An IP is an address in the internet. if your address is public. you have to expect some trespassers !
If you have proxy in your DNS setup in Cloudflare, your IP address will not be available for public.
Even though most people enable the proxy, They forgot the MOST IMPORTANT PART !!!. Yes the network!. imagine a situation: show how your IP address of the Web-server has exposed. So attackers can sent a lost of requests to your ip and they can bypass the Cloudflare WAF by adding an entry in:/etc/hosts22.222.333.444 your domain.com
so they can send request to the origin server without Cloudflare. So cloudlfare won’t be able to protect your website!
What is the solution?
The solution is quite simple. Restrict the incoming web requests to Cloudflare (port 80 and 443). As we mentioned above the traffic must be served through Cloudflare network only. Cloudlfare will only connect to our servers from their specified range of IPs. IP rages are available here. But adding those records to your UFW manually is bit risk and time-consuming.
For adding those to UFW you can use the following script :
#!/bin/sh cd /tmp wget https://www.cloudflare.com/ips-v4 -O ips-v4-$$.tmp wget https://www.cloudflare.com/ips-v6 -O ips-v6-$$.tmp for cfip in `cat ips-v4-$$.tmp`; do echo "ufw allow from $cfip to any port 443 proto tcp"; done for cfip in `cat ips-v6-$$.tmp`; do echo "ufw allow from $cfip to any port 443 proto tcp"; done
Do you want to add these rules to your AWS security group, well! we have a anther script for that too…
Hope you have AWS CLI access. So you can run the following script from your terminal.
change SG_ID to your security group that you need to update.
# first we download the list of IP ranges from CloudFlare
wget https://www.cloudflare.com/ips-v4
# set the security group ID
SG_ID="sg-00000000000000"
# iterate over the IP ranges in the downloaded file
# and allow access to ports 80 and 443
while read p
do
aws ec2 authorize-security-group-ingress --group-id $SG_ID --ip-permissions IpProtocol=tcp,FromPort=80,ToPort=80,IpRanges="[{CidrIp=$p,Description='Cloudflare'}]"
aws ec2 authorize-security-group-ingress --group-id $SG_ID --ip-permissions IpProtocol=tcp,FromPort=443,ToPort=443,IpRanges="[{CidrIp=$p,Description='Cloudflare'}]"
done< ips-v4
rm ips-v4If you don’t have AWS CLI access, run it from AWS cloud shell form the AWS console itself.
Hope you Enjoyed the reading!